Scale your business’s security as you grow
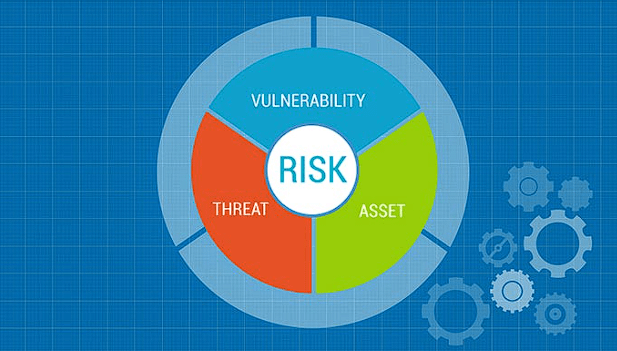
As defenders, the objective is to stop an adversary from achieving their goal. These adversaries are using both their own trade craft and other methods to launch attacks against organisations.
This module will explore the various tools and methodologies that will help defenders keep up with the latest threat intelligence to understand how adversaries are operating and apply it to your defense strategy.